Privacy & Security for Zoom Video Communications
Zoom keeps privacy and security top of mind for all end users. Find resources and features on how Zoom secures your data and protects your privacy.

If you think you have found a security vulnerability in Zoom, please visit our Vulnerability Disclosure Policy.

Please join us for a candid conversation
with CEO Eric S. Yuan and other senior Zoom executives and advisors as we anwer your questions
live.
Register
Now
View
Most Recent Recording
 Zoom Rolling Out End-to-End Encryption Offering
Zoom Rolling Out End-to-End Encryption Offering
 Secure Your Zoom Account with Two-Factor Authentication
Secure Your Zoom Account with Two-Factor Authentication
 Zoom to Open R&D Centers in Phoenix and Pittsburgh
Zoom to Open R&D Centers in Phoenix and Pittsburgh
 Zoom Acquires Keybase, Announces Goal of Enterprise End-to-End Encryption Offering
Zoom Acquires Keybase, Announces Goal of Enterprise End-to-End Encryption Offering
 Zoom Adds Board Member H.R. McMaster, Jonathan Kallmer to Leadership Team
Zoom Adds Board Member H.R. McMaster, Jonathan Kallmer to Leadership Team
 Zoom Releases Zoom 5.0
Zoom Releases Zoom 5.0

 Best Practices for Securing Your Virtual Classroom
Best Practices for Securing Your Virtual Classroom
 How to Keep Uninvited Guests Out of Your Zoom Event
How to Keep Uninvited Guests Out of Your Zoom Event
 A Letter from Zoom’s Management Team to Our Customers
A Letter from Zoom’s Management Team to Our Customers
 Zoom Security White Paper
Zoom Security White Paper
 Encryption White Paper
Encryption White Paper
 Client Connections Process
Client Connections Process
 Securing Your Zoom
Securing Your ZoomMeetings

Pre-Meeting Settings
Securing your Zoom Meetings can start before your event even begins, with a robust set of pre-meeting features.
- Waiting Rooms: IT Admins can enforce waiting rooms at the account, group, or user level. You can also require them for all participants, or just for guests not included in your account. If made optional, meeting hosts can enable Waiting Rooms in the “Settings” menu of their Zoom profile.
- Passcodes: Passcodes can be set at the individual meeting level or can be enabled at the user, group, or account level for all meetings and webinars. Account owners and admins can also lock passcode settings, to require passcodes for all meetings and webinars on their account.
- Join by Domain: Only authenticated users can join meetings which requires individuals to sign into a zoom account and/or ensure their e-mail address is on an approved list before allowing them to join.
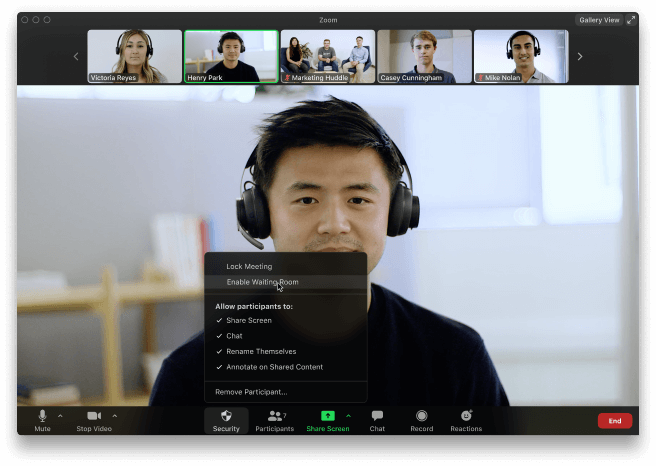
In-Meeting Settings
Zoom has controls at your fingertips to ensure your meetings are secure and disruption-free.
- Security options in toolbar: Meeting hosts have a Security icon in the toolbar for quick access to essential in-meeting security controls. See it in action!
- Lock the meeting: When a host locks a Zoom Meeting that’s already started, no new participants can join, even if they have the meeting ID and passcode (if you have required one).
- Put participant on hold: You can put an attendee on hold and their video and audio connections will be disabled momentarily.
- Remove participants: From that Participants menu, you can mouse over a participant’s name, and several options will appear, including “Remove”.
- Report a user: Hosts/co-hosts can report users to Zoom’s Trust & Safety team, who will review any potential misuse of the platform and take appropriate action.
- Disable video: Hosts can turn someone’s video off. This will allow hosts to block unwanted, distracting, or inappropriate gestures on video.
- Mute participants: Hosts can mute/unmute individual participants or all of them at once. Hosts can block unwanted, distracting, or inappropriate noise from other participants. You can also enable “Mute Upon Entry” in your settings, which is a good option for large meetings.
- Turn off file transfer: In-meeting file transfer allows people to share files through the in-meeting chat.
- Turn off annotation: You can disable the annotation feature in your Zoom settings to prevent people from writing all over the screens.
- Disable private chat: Zoom has in-meeting chat for everyone or participants can message each other privately. Restrict participants’ ability to chat amongst one another while your event is going on and cut back on distractions.
- Control screen sharing: The meeting host can turn off screen sharing for participants.
- Control recording: The ability to record to the cloud or locally is something an account admin can control. If they have recording access, the host can decide to enable/disable a participant or all participants to record.
- Do not allow participants to rename their ID: The host can disable the ability for participants to rename their onscreen identity.
- Turn on waiting rooms: The meeting host can turn on waiting rooms from within the meeting.
Protecting your data
You are entrusting us with your valuable data and information and we take great care to ensure your data is secure at all times.
- Encryption: Protecting your event content by encrypting the session’s video, audio, and screen sharing. This content is protected with the Advanced Encryption Standard (AES) 256 using a one-time key for that specific session when using a Zoom client. Optional end-to-end encryption ensures that no third party -- including Zoom -- has access to the meeting’s private keys. End-to-end encryption will be generally available as a technical preview, which means we’re proactively soliciting feedback from users for the first 30 days.
- Audio Signatures: Embeds a user's personal information into the audio as an inaudible watermark if they record during a meeting. If the audio file is shared without permission, Zoom can help identify which participant recorded the meeting.
- Watermark Screenshots: Superimposes an image, consisting of a portion of a meeting participant’s own email address, onto the shared content they are viewing and the video of the person who is sharing their screen.
- Local Recording Storage: Recordings stored locally on the host’s device can be encrypted if desired using various free or commercially available tools.
- Cloud Recording Storage: Cloud Recordings are processed and stored in Zoom’s cloud after the meeting has ended; these recordings can be passcode-protected or available only to people in your organization. If a meeting host enables cloud recording and audio transcripts, both will be stored encrypted.
- File transfer storage: If a meeting host enables file transfer through in-meeting chat, those shared files will be stored encrypted and will be deleted within 31 days of the meeting.
- Cloud recording access: Meeting recording access is limited to the meeting host and account admin. The meeting/webinar host authorizes others to access the recording with options to share publicly, internal-only, add registration to view, enable/disable ability to download, and an option to protect the recording.

Security and Privacy Certifications
We are recognized by industry and security organizations for excellence.
- SOC 2 (Type II)
- FedRAMP (Moderate)
- GDPR, CCPA, COPPA, FERPA and HIPAA Compliant (with BAA)
- International Association of Privacy Professionals (IAPP) Silver Member
- Zoom’s security controls also align with the UK National Cyber Security Centre’s (NCSC) cloud security principles
Ensuring Privacy
Zoom takes your privacy extremely seriously and only collects the data from individuals using the Zoom platform required to provide the service and ensure it is delivered effectively. See our privacy policy here.
- Authentication: Zoom offers a range of authentication methods such as SAML, Google Sign-in and Facebook Login, and/or Password based which can be individually enabled/disabled for an account.
- 2-Factor Authentication: Admins can enable 2FA for your users, requiring them to set up and use 2FA to access the Zoom web portal.
- Video Preview: Before you join a meeting, you can preview your video and select a virtual background, or decide to join without video.
- Attendee consent for recording: Account admins or meeting hosts can require that all recordings of meetings are accompanied by a pop-up notice to attendees that a recording is taking place, and there is a visual indicator when recording is on.
- Removed Attention Tracking: Zoom recently removed the option for training professionals to track if attendees were multi-tasking during a meeting.
- Meeting participants’ basic technical information: (Such as the user’s IP address, OS details, and device details) is collected for troubleshooting and admin reporting.
- Zoom stores basic information: Under user account profile information including: Email address, user password - salted, hashed, first and last name. Company name, phone number, and a profile picture are all optional to provide.
- We never have, and have no future intentions, to sell your information to advertisers.
- Zoom does not monitor your meetings or its contents.
- Zoom complies with all applicable privacy laws, rules, and regulations in the jurisdictions in which it operates, including the GDPR and the CCPA.
Hear what 3rd parties are saying
In the effort to present a balanced view, these articles offer a level-headed, thoughtful analysis of Zoom’s security and privacy.

Beyond the noise — 7 reasons it’s safe to run Zoom by Rowan Trollope

Zooming to Conclusions by Vince Crisler

Video service Zoom taking security seriously -U.S. government memo from U.S. Department of Homeland Security by Raphael Satter and Christopher Bing

The Strange Zoom Pile-on by Robert Walker

Zoom Security: Everything That Home Users And IT Teams Need To Know by Former White House CIO Theresa Payton

It’s time to stop bashing Zoom by Jerry Bowles
